2024浙江省省赛复现
1.2024浙江省赛复现
1.real signin
得到一张out.png,用zsteg跑一下发现:

得到
1 | dEFfc1dGq1pxMgMWnihrMx9mewNgdvIWMvctrc |
和
1 | ABCDEFGHIJKLMNabcdefghijklmnopqrstuvwxyzOPQRSTUVWXYZ0123456789+/ |
猜测是换表的base64,解密得到flag:DASCTF{We1C0me_2_ZJCTF2024!}
2.机密文档
得到一个加密的压缩包,发现加密方式是store,猜测为明文攻击

[!NOTE]
将一个名为flag.txt的文件打包成ZIP压缩包后,发现文件名称会出现在压缩包文件头中,且偏移固定为30
且默认情况下,flag.zip也会作为该压缩包的名称
已知的明文片段有:
“flag.txt” 8个字节,偏移30
ZIP本身文件头:50 4B 03 04 ,4字节
满足12字节的要求
其中 -C 后面跟的是原本的zip,-c 后面跟的是里面需要解密出来的zip,-x 后面是已知的明文,30 表示偏移量,7468655F7365637265745F796F755F6E657665725F657665725F6B6E6F775F6861686168616861是the_secret_you_never_ever_know_hahahaha的16进制转换,即用010打开后看到的。下一个 -x 0 是zip的偏移量,504B0304是zip的16进制表示。
可以看到解压出来的keys是
1 | b8edf1ff c1f93a7e f93d08e0 |
得到三段密钥就可以修改压缩包密码了:

修改了密码为123
解压后得到一个docm文档,猜测是跟宏有关的,wps打开发现

这里可以使用wps里查看宏,也可以olevba看
wps 里查看如下:

olevba 查看如下:

反正最后得到如下宏代码:
1 | Sub key() |
可以发现是一个异或代码,可以手搓脚本解密,也可以cyberchef
cyberchef得到如下:

1 | ulhged98BhgVHYp |
由于之前提示了是outguess加密,将docm后缀改为zip后在 word / media 里拿到图片 image1.jpeg
由于outguess不认识jpeg,需要我们修改后缀名为jpg
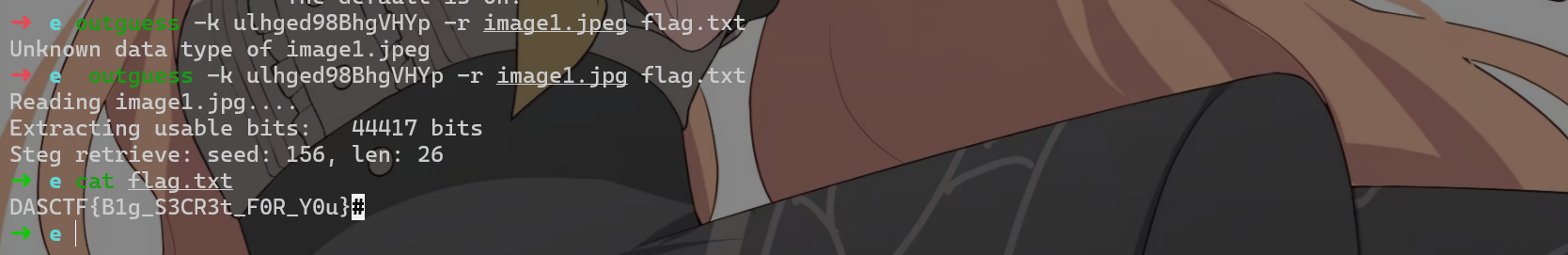
得到flag:DASCTF{B1g_S3CR3t_F0R_Y0u}
3.EZtraffic
拿到流量分析一下就可以在SMB里发现有传输流量包,导出一下

发现有三个压缩包,但是只有其中一个是final_out,即最后的zip
这里最好不要用foremost和binwalk,因为你会发现导出的压缩包里面会少东西。
打开压缩包发现

注释
1 | NTLM v2 plaintext + \d{5} |
这里后来才知道需要提取 NTLMv2 哈希值并破解,可以看lunatic师傅的博客 这里
而且这里 + \d{5} 提示后面再跟五位数字爆破。
这里可以用tshark导出(tshark是kali自带的)
1 | tshark -n -r eztraffic.pcapng -Y 'ntlmssp.messagetype == 0x00000003' -T fields -e ntlmssp.auth.username -e ntlmssp.auth.domain -e ntlmssp.ntlmv2_response.ntproofstr -e ntlmssp.auth.sesskey -e smb2.sesid |
得到

这里我们需要的是username::domain:ServerChallenge:NTproofstring:modifiedntlmv2response并且需要以这个形式保存到txt里
1 | rockyou #username |
先过滤
1 | ntlmssp |
可以看到很多流,其中有一个是NTLMSSP_AUTH的
在里面找NTLMv2 Response,可以看到

除了NTProofStr以外的就是我们要找的modifiedntlmv2response了(注意这里复制hex值)
最后得到
1 | rockyou::MicrosoftAccount:4936df20962cae6d:db12ced50faf52f141636e80205e8f28:01010000000000003604281b951fdb017b4045aa008508eb0000000002001e00440042004500440036004200350041002d0035003100430032002d00340001001e00440042004500440036004200350041002d0035003100430032002d00340004004800640062006500640036006200350061002d0035003100630032002d0034003100650063002d0061006400380034002d0064006400320062003500370030006400350030003900360003004800640062006500640036006200350061002d0035003100630032002d0034003100650063002d0061006400380034002d00640064003200620035003700300064003500300039003600070008003604281b951fdb01060004000200000008003000300000000000000001000000002000008029a5d8256e5c2762f439df5c06f3bc411fb0faeb3a6fa52d9273c57b09f2d10a0010000000000000000000000000000000000009001e0063006900660073002f00310030002e00310030002e0031002e00380031000000000000000000 |
将以上的内容保存到hash.txt中,用hashcat爆破,命令
1 | .\hashcat -m 5600 hash.txt rockyou.txt |

得到密码
1 | haticehatice |
接下来就是5位掩码爆破了,ARP秒出

得到密码haticehatice12580,解压压缩包,看到有100张图片碎片,猜测是拼图

猜测图片应该是有顺序的,不然也太难拼了
在stegsolve的rad0里看到

QCR扫一下,看到

这里需要我们按照顺序一个个的把图片更改一下
利用脚本拼接一下(脚本抄的。)
1 | from PIL import Image |
最后得到

4.FinalSign
文章能看到的:
1 | 2c243f2f3b3114345d0a0909333f06100143023b2c55020912 |
可以发现文章里有雪隐写,里面隐写了xor的密码:

接下来cyberchef就能出了

5.非黑即白
得到一个没有后缀的文件,010打开发现是逆序的gif
利用puzzlesolver逆序回来,得到gif,再拆分一下发现全是黑白图片:

这里应该是二进制,脚本提取一下(脚本借鉴的。。):
1 | import hashlib |
这个需要放在文件同目录下,得到
1 | 010100000100101100000011000001000001010000000000000000010000000000000000000000001110101101011000010110010101100110011101110010111100011110011010001010100000000000000000000000000001111000000000000000000000000000001000000000000000000000000000011001100110110001100001011001110010111001110100011110000111010011110111100011000101111101011100101100011111010111101011001110111011111100000011011000010010111010010100010101110011110000101000000001011101110000101101101111111111010011001000001111111101001010100111110011110011101001100011011000001110111001110001011101111111101100000110101011010110101110101100001001100000100010101011010111100001000001010000010010110000000100000010001111110000000000010100000000000000000100000000000000000000000011101011010110000101100101011001100111011100101111000111100110100010101000000000000000000000000000011110000000000000000000000000000010000000000000100100000000000000000000000000000000000000000000000000000000000010000000000000000000000000000000000000000000000000000000000000011001100110110001100001011001110010111001110100011110000111010000001010000000000010000000000000000000000000000000000000000000000000000100000000000110000000000001011000011101010101010000000001100010110010011011011011000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001010000010010110000010100000110000000000000000000000000000000000000000100000000000000010000000001011010000000000000000000000000010100000000000000000000000000000000000000000000 |
放在cyberchef里可以看到是一个压缩包,下载下来

gif的帧间隔里隐藏了密码

要删除最后一个0,使用 cyberchef 转 ascii 码得到:

用密码解压zip得到flag:DASCTF{H3r3_1s_C0L0rful_W0rld}
6.天命人
得到zip里面是6个文件,解压之后用010打开发现是一个zip打乱了顺序分成了6个
脚本使其重新成为一个zip:(这里需要我们手动重命名顺序)
1 | with open("1","rb") as f: |
得到一个zip,解压出来是两个有密码的zip文件

可以发现根器里面的txt很小,只有4字节,利用crc爆破一下(注意要重命名,不能出现中文

得到:C0M3_4ND_Get_S1X_R00TS!!
解压未竟zip,发现金箍棒图片是要我们手提像素点,利用脚本
1 | import os |
1 | python get_pixels.py -f 1.png -p 5x5+1915x1075 -n 10x10 |
得到:

这个是veracrypt加密的磁盘文件,需要我们挂载
挂载需要密钥。密钥文件

然后点加载,就能在z盘里看到flag